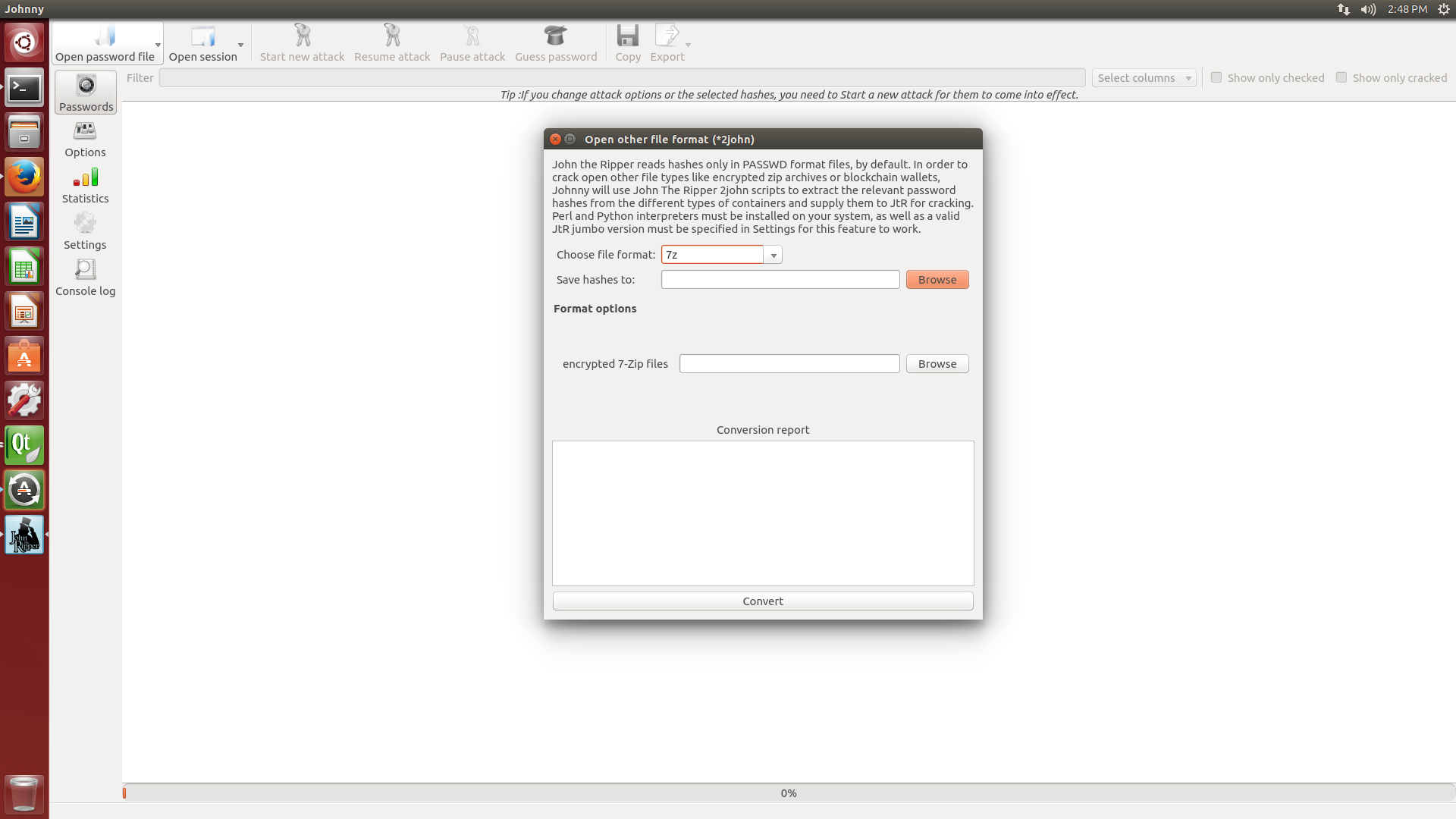
John The Ripper Dmg
John the Ripper is part of Owl, Debian GNU/Linux, Fedora Linux, Gentoo Linux, Mandriva Linux, SUSE Linux, and a number of other Linux distributions. It is in the ports/packages collections of FreeBSD, NetBSD, and OpenBSD. John the Ripper is a registered project with Open Hub and it is listed at SecTools. John The Ripper: Cracking a.DMG Let's cut to the chase right now: Cracking encrypted disk image, AKA DMG is feasible, but, and there are many buts, is extremely, extremely time consuming. $ GWS=8192./john -form:dmg-opencl hashfile (first '$' being the prompt). Like @mledford says you can use -fork since your compiler apparently doesn't want to build OMP. But this is only applicable for -format:dmg, not -format=dmg-opencl - if you try to fork several processes using same GPU card it will probably not end up well. John is a state of the art offline password cracking tool. John was better known as John The Ripper(JTR) combines many forms of password crackers into one single tool. It automatically detects the type of password & tries to crack them with either bruteforceing the encrypted hash or by using a dictionary attack on it.
John the Ripper is an Open Source password security auditing and password recovery tool available for many operating systems.John the Ripper jumbo supports hundreds of hash and cipher types, including for: user passwords of Unix flavors(Linux, *BSD, Solaris, AIX, QNX, etc.), macOS, Windows, 'web apps' (e.g., WordPress), groupware (e.g., Notes/Domino), anddatabase servers (SQL, LDAP, etc.);network traffic captures (Windows network authentication, WiFi WPA-PSK, etc.);encrypted private keys (SSH, GnuPG, cryptocurrency wallets, etc.),filesystems and disks (macOS .dmg files and 'sparse bundles', Windows BitLocker, etc.),archives (ZIP, RAR, 7z), and document files (PDF, Microsoft Office's, etc.)These are just some of the examples - there are many more. |
John the Ripper is an Open Source password security auditing and password recovery tool available for many operating systems. John the Ripper jumbo supports hundreds of hash and cipher types, including for: user passwords of Unix flavors (Linux,.BSD, Solaris, AIX, QNX, etc.), macOS, Windows, 'web apps' (e.g., WordPress), groupware (e.g., Notes.
|
As an alternative to running John the Ripper on your own computer, you can run it in the cloud.We provide a pre-generated Amazon Machine Image (AMI) calledOpenwall Password Recovery and Password Security Auditing Bundle,which lets you start password recovery or a password security audit in minutes(if you've used Amazon Web Services before, or you need tosign up first).
The Bundle features Amazon Linux 2 along with John the Ripper jumbo pre-built and pre-configuredwith multi-GPU (via OpenCL) and multi-CPU support (with AVX-512, AVX2, and AVX acceleration,and transparent fallback when run on older CPUs lacking the latest AVX extensions).The Bundle has been tested on both GPU-enabled and CPU-only AWS instances.
Also included are the 'all.lst' multi-lingual wordlist (20+ languages) from theOpenwall wordlists collection,and sample Unix and Windows password hashes for testing and learning how to use the software.
Proceed to subscribe to the Bundle and launch your first virtual machine:
- Openwall Password Recovery and Password Security Auditing Bundle in AWS Marketplace
available under our End-User License Agreement
Paid usage of the Bundle supports our Open Source project.In fact, this might be one of your reasons to use the Bundle as opposed to building from source on your own,especially if you manage an AWS account for an organization that benefits from our software andcan afford to contribute back.
For hash and cipher types that we include OpenCL support for,we recommend current generation GPU instance typep3.2xlarge (or larger), which features NVIDIA Tesla V100 GPU(s).For hash and cipher types that we only support on CPU and in special cases where CPUs are more efficient,we recommend current generation Compute Optimized instance typesc5.24xlarge (Intel Xeon, AVX-512) orc5a.24xlarge (AMD EPYC, AVX2).If in doubt, give several of these a try at your specific task.
Connect to your instanceusing a SSH client(on Windows, you canuse PuTTY).To keep and reconnect to a running John the Ripper session across SSH disconnects/reconnects,use one of the toolsscreen ortmux,both of which are pre-installed in our AMI.
For major cost savings, we recommendspot instances,where you bid a maximum per hour price and are charged the current market price.A typical spot price is 2 to 3+ times lower than the regular on-demand price.(This applies to AWS service fees only.The charges for our Bundle are on top of those, and are the same for spot and on-demand instances.Nevertheless, you'd typically halve your total costs by using spot instances.)When launching from AWS Marketplace, choose 'Launch through EC2' instead of 'Launch from Website'.This gets you to 7-step 'Launch instance wizard'.On 'Step 3: Configure Instance Details',check the 'Request Spot instances' box and enter a 'Maximum price' no lower than one of the current prices.Under 'Subnet', choose an option matching an 'Availability Zone' for which a low enough current price was listed.
A spot instance might be interrupted if the market price exceeds your bid.One way not to lose your work-in-progress if a spot instance gets interrupted is to uncheck the 'Delete on Termination' box on'Step 4: Add Storage'.You can then effectivelyrecover your instance by creating a snapshot from the terminated instance's volume, creating an AMI from the snapshot,and launching an instance from the AMI.You'll need to run the 'john --restore' command to continue from where the work was interrupted.
If you're new to AWS, you'll likely find that you need torequest a service quota increase before you're able to launch the large instances that we recommend,and to launch them as spot instances.
We don't charge for usage of the Bundle on nano and micro sized instances.Out of those, t2.micro is eligible for AWS free tier,which provides free usage of some AWS services for the first year for new AWS users.Outside of the free tier, t3.micro is better.Of course, such instances are unsuitable for serious usage of the Bundle(especially as they're so-called 'burstable' instances, with long-term vCPU utilizationlimited e.g. to just 10% of one vCPU on t2.micro),but you can use them for getting acquainted with the Bundle at no or little cost,and they just might succeed in recovering the weakest passwords despite of being extremely limited performance-wise.Once your service quota permits, we recommend at least c5.large (which isn't 'burstable', allowing sustained 100% vCPU utilization).
For free community support on (semi-)advanced questions or issues (if you know half the answer),please join the publicjohn-users mailing listand post in there.For general customer support, please e-mail us at <john-cloud-support at openwall.com>.
You can browse the documentation for John the Ripper core online.Also relevant is ourpresentation on the history of password security.
Screenshots of a terminal window accessing an AWS p3.2xlarge instance
Basic usage instructions, and md5crypt benchmark on an NVIDIA Tesla V100 GPU on AWS as an illustration of performance to expect:Demo of Apple macOS .dmg file password recovery using a GPU in the cloud:
52393 |
John the Ripper (JtR) is one of the hacking tools the Varonis IR Team used in the first Live Cyber Attack demo, and one of the most popular password cracking programs out there. In this blog post, we are going to dive into John the Ripper, show you how it works, and explain why it’s important.
Notes about hacking: Hacking is a pursuit of knowledge about systems, design, and humans. In this case, we are talking about software and operating systems.
Get the Free Pen Testing Active Directory Environments EBook
Hacking is not necessarily criminal, although it can be a tool used for bad intentions. We advocate for ethical hacking. Stay in the light side of the Force.
How Does John the Ripper Work?
JtR supports several common encryption technologies out-of-the-box for UNIX and Windows-based systems. (ed. Mac is UNIX based). JtR autodetects the encryption on the hashed data and compares it against a large plain-text file that contains popular passwords, hashing each password, and then stopping it when it finds a match. Simple.
In our amazing Live Cyber Attack demo, the Varonis IR team demonstrates how to steal a hashed password, use JtR to find the true password, and use it to log into an administrative account. That is a very common use case for JtR!
JtR also includes its own wordlists of common passwords for 20+ languages. These wordlists provide JtR with thousands of possible passwords from which it can generate the corresponding hash values to make a high-value guess of the target password. Since most people choose easy-to-remember passwords, JtR is often very effective even with its out-of-the-box wordlists of passwords.
JtR is included in the pentesting versions of Kali Linux.
What is John the Ripper Used for?
JtR is primarily a password cracker used during pentesting exercises that can help IT staff spot weak passwords and poor password policies.
Here is the list of encryption technologies found in JtR:
- UNIX crypt(3)
- Traditional DES-based
- “bigcrypt”
- BSDI extended DES-based
- FreeBSD MD5-based (linux and Cisco IOS)
- OpenBSD Blowfish-based
- Kerberos/AFS
- Windows LM (DES-based)
- DES-based tripcodes
- SHA-crypt hashes (newer versions of Fedora and Ubuntu)
- SHA-crypt and SUNMD5 hashes (Solaris)
That’s the “official” list. JtR is open-source, so if your encryption of choice isn’t on the list do some digging. Someone might have already written an extension for it.
How to Download John the Ripper
JtR is an open-source project, so you can either download and compile the source on your own, download the executable binaries, or find it as part of a penetration testing package.
The official website for John the Ripper is on Openwall. You can grab the source code and binaries there, and you can join the GitHub to contribute to the project.
JtR is available on Kali Linux as part of their password cracking metapackages.
Tutorials for Using John the Ripper
We are going to go over several of the basic commands that you need to know to start using John the Ripper. To get started all you need is a file that contains a hash value to decrypt.
If you ever need to see a list of commands in JtR, run this command:
Cracking Passwords
John the Ripper’s primary modes to crack passwords are single crack mode, wordlist mode, and incremental. The single crack mode is the fastest and best mode if you have a full password file to crack. Wordlist mode compares the hash to a known list of potential password matches. Incremental mode is the most powerful and possibly won’t complete. This is your classic brute force mode that tries every possible character combination until you have a possible result.
The easiest way to try cracking a password is to let JtR go through a series of common cracking modes. This command below tells JtR to try “simple” mode, then the default wordlists containing likely passwords, and then “incremental” mode.
You can also download different wordlists from the Internet, and you can create your own new wordlists for JtR to use with the –wordlist parameter.
If you want to specify a cracking mode use the exact parameter for the mode.
Word Mangling Rules
Mangling is a preprocessor in JtR that optimizes the wordlist to make the cracking process faster. Use the –rules parameter to set the mangling rules.
John The Ripper Dmg2john
Viewing Your Output
When you want to see the list of passwords that you have cracked, use the –show parameter.
John The Ripper Dmg Game
If your cracked password list is long, you can filter the list with additional parameters. You can also redirect the output using basic redirection in your shell. For example, if you want to see if you cracked any root users (UID=0) use the –users parameter.
Or if you want to show users from privileged groups use –groups.
Below is the JtR command from our Live Cyber Attack Webinar. In this scenario, our hacker used kerberoast to steal a Kerberos ticket granting ticket(TGT) containing the hash to be cracked, which was saved in a file called ticket.txt. In our case, the wordlist used is the classic rockyou password file from Kali Linux, and the command was set to report progress every 3 seconds.


John The Ripper Dmg Youtube
If you want to see some cool pentesting and defense tactics using Varonis, check out the Live Cyber Attack Webinars! Pick any time that works for you!