Prodiscover Basic
ProDiscover Basic vs. ENCASE Enterprise. Encase-Approx $3,000. Pro Discover- Free. Can accomplish the same things however each has a few different tools. ENCASE Enterprise can actually read information over a network using P2P. Pro Discover needs to have a disk present to view. ProDiscover Basic edition is the free member of the ProDiscover family for hard disk security examination. It may not be as comprehensive as the other two products in the family, but it will give you an idea of the great potential these suite of products have.
Advanced Computer Forensics
Windows ProDiscover Forensics Lab
Prodiscover basic software. More Apple Software Update 2.6.3.1. 84.2MB - Shareware - Apple Software Update is a software tool by Apple that installs the. ProDiscover Basic. ProDiscover Basic is a simple digital forensic investigation tool that has tools for images, analysis, and reports on evidence found on drives. The Sleuth Kit is an open source digital forensics toolkit that can be used to perform in-depth analysis of various file systems. Autopsy is a GUI for The Sleuth Kit. ProDiscover Basic. A digital forensic investigation tool to image, analyze, and report on evidence found on a drive. The data can be viewed by content or by looking at the clusters that hold the data. Data can be searched for specific information (Tabona, 2013). Tool by Access Data for data preview and hard drive imaging.
This lab is a replacement for the EnCase lab (122) for students who have been unable to access EnCase through RLES. In order to do this lab, you will need to download and install ProDiscover Basic (make sure to pick 32-bit or 64-bit depending on your version of Windows) from this URL: http://www.techpathways.com/desktopdefault.aspx?tabindex=8&tabid=14 (scroll down until you see the download links at the bottom of the page). You will also need to download a copy of the image files for this lab, 123img.zip. These image files are distributed under the GPL and were originally created by Brian Carrier.
Instructions appear as bullet points, questions are numbered and bolded.
Instructions & Questions
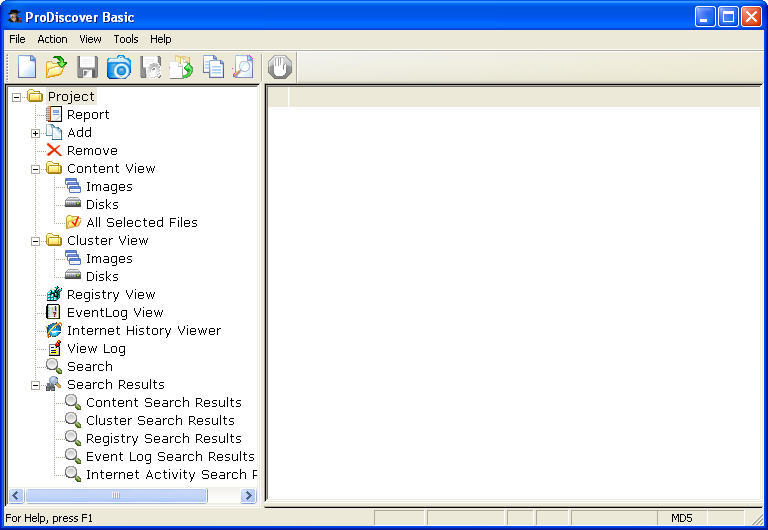
- Start ProDiscover Basic.
- Create a new project for this laboratory. Give it a unique number and name.
- Click “Add” then “Image File” and add “123img1.dd”.
- Click the “Action” menu then generate “OS Info”. This adds some information about the image to the report, which you can view at any time during your examination by clicking on “View” then “Report”.
- What is the file system of this image file?
- What is the volume name?
- Go to “Cluster View” and click on the image.
- How many clusters are used on this image file?
- Go to “Content View” and click on the image.
- List all the Deleted files recovered by ProDiscover in a table – and calculate the MD5 hash value for each deleted file.
- Is there anything special about any of the files?
- ProDiscover will use the time zone setting of your examiner workstation if no time zone is set for the evidence. When you acquire a computer as evidence it is important to make note of the computer’s time and time zone, especially if you need to correlate evidence from different time zones (never assume the time or time zone on a computer is correct.)
- Where does the Time Zone information reside in a Windows system?
- Set the timezone by clicking on File, then Preferences. The timezone should be US Central Time in this particular case (the image file has been extracted from a computer in that timezone although it is not an image of the system partition so there is no way to find the computer’s actual timezone from the image itself).

- What is the latest file creation time on the image?
- Which files are resident files? Hint: you can right-click on a file and say “Show Cluster Numbers” to see the cluster/s in which the file is stored – you can do this for the $MFT of the disk image to see which clusters are allocated to the $MFT.
- Add the second image to the case – “123img2.dd”
- Go to the “Content View” and click “All Files”.
- Go to the “View” menu and select “Gallery View”.
- Which files display a thumbnail in Gallery View?
- Are there any files with mismatching file extensions? If so, which ones? Identify their types according to their extension versus their actual type and explain how you have identified the actual type.

- Disable Gallery View.
- Extract all JPEG files from the image by selecting each of them. You will be prompted to add a comment about the file for the report. Record “JPEG file” and whether the file has been hidden, deleted, mislabelled or is in any other way special.
- Right-click on a file and click “Copy All Selected Files”. Save them in a temporary directory on your computer.
- Paste each JPEG file from your temporary directory into your submission document as an embedded image.
- Do you think you have identified every JPEG file in the image? Hint: You can search for the JPEG file header by clicking on “Search”, selecting “Hex” and searching for the pattern FFD8. Do any files contain the pattern which do not appear in your temporary directory? If so, which ones?
- Create a table for all files on the second image, listing each file’s name and MD5 hash value.
Your answers to all questions should be stored in a LibreOffice document, Word document or PDF, and uploaded to Dropbox in the “EnCase Lab” folder as this exercise replaces the EnCase lab.
Video Summarizing the Problem
Response from Creator of ProDiscover
I notified Chris Brown privately, and he responded withthis message within 2 days. I really appreciate hisfast and intelligent reply!I don't completely understand the explanation--it doesn'tseem like this is the whole problem. But I'll bevery interested tosee the updated version and test it.
We have reviewed and tested the issues you reported. The first issue is problem with reading first two clusters in FAT12 partitions. In FAT12, cluster numbers start with 2, the 0th cluster being the boot information and the first cluster is directory structure. We were not handling them properly in that we were only reading first 512 bytes (one sector) of these group of sectors and displaying information. We have fixed this issue by handling reading logic for the first two clusters.The issue with the logical floppy secure wipe was that we are using a third party algorithm to erase logical disks, to be DoD compliant for logical secure wipes. This 'canned algorithm' is creating problem. Suppose, a file of 512 bytes is saved, then it occupies more than one sector on the disk. The algorithm we were using is only erasing 512 bytes. We have corrected this and will round the file size to the cluster boundary, which will fix the problem. BTW, the logical secure wipe is an old concept (as old as floppy disks) of writing random data to a logical file system. This process is only provided for DoD spec requirements and is not recommended for use in Forensics. I would always recommend wiping a disk at the physical level with a known pattern. This process ensures that you wipe any unallocated/slack space ad is visually verifiable.
Thank you for taking the time to report these issues. They are both corrected and will release with the next product update.
Christopher L. T. Brown, CISSP, DFCP
Technology Pathways LLC
Founder & CTO
Details of Other Tests
Vendor Notification
Cluster Contents Incorrect
I am using a floppy disk image from honeynet:I am using Windows 7 in a Fusion virtual machine,on a Mac OS X host.
I downloaded it, verified the MD5, and unzipped it.
Here's the MD5 hash of the unzipped image.dd raw file:
I started ProDiscover Basic and loaded the image.dd file.
Here's the version of ProDiscover I used:
I viewed the image.dd file in Cluster view, which showsthe raw data in hex.
Here's the first sector--the MBR:
Here's the second sector--the start of the FAT.It begins with the three bytes F0 FF FF, as explainedhere:
This article tells me to expect the second copy of the FATin sector ten (0A in hex):
But this is what ProDiscover shows in sector A--theF0 FF FF is not there!
I tried a Search to find it:
The results say it should be in cluster A.
What's going on? I opened the original image.ddfile in HxD, a simple hex editor.
Here's sector 1, starting with the F0 FF FF:
Here's sector 10, starting with the F0 FF FF:
HxD also shows that all the sectors between 1 and 10 areempty--filled with 00 bytes.
But ProDiscover shows them filled with data,like this:
What's going on? What am I doing wrong?
Failure to Wipe Floppy Disk
I made a new empty .flp filelike this:This procedure was recommended here:
I connected the virtual floppy to aVMware Windows 7 machine, formatted the floppy,and filled it with text files containing manyrepeats of the word 'SPAM':
HxD shows the SPAM on the floppy:
I used ProDiscover Basic's 'Tools', 'Secure Wipe'function:
I expected the disk to be zeroed, but that'snot what ProDiscover did.
The MBR is still there:
The first FAT contains the F0 FF FF mark, but nothingelse:
The second FAT also contains the F0 FF FF mark, but nothingelse:
The root directory still contains most of anold filename 'SPAM.TXT':
This might seem like a small problem, but it'snot! The 'Secure Wipe' did not eraseall the data, it just overwrote the active data.Here's what ProDiscover did to thecontents of the SPAM files:
Now let's test this using a floppy diskwith a corrupted FAT, which I got here:
This floppy contains data of a potentiallysensitive nature.
Here's some sensitive text:
Here we see the end of a JPGimage, with the end-of-file mark FF D9,followed by a password:
(I redacted the image to avoid interfering withstudents doing the Honeynet challenge.)
I ran the ProDiscover 'Secure Wipe'on this disk, and here's the result:
The text has been overwritten:
But the other data remains on the disk:
(I redacted the image to avoid interfering withstudents doing the Honeynet challenge.)
This is not a proper forensic wipe at all!
Using Windows XP and a Real Hard Disk
I tested this using a real computer, not a virtualmachine, running Windows XP, and using a realhard disk, not a floppy disk.I made an 8 MB FAT-16 partition on the disk:
I filled it with SPAM:
It's almost completely full:
The directory structure for FAT-16 shows thatthe starting cluster is at an offset of0x1a, starting from the first characterin the filename:
Here's the directory, viewed in the HxD hexeditor.
The directory entry for theSPAM.TXT file starts at byte 10080 withthe file name.
Bytes 1009A and 1009B contain the addressof the first cluster. Right now they hold02 00.
In the hex editor, I changed byte1009A to 00. This creates an incorrectcluster number of 00 00.
I made a new project in ProDiscover and addedthe physical hard drive.

ProDiscover now shows sector 2 filled with SPAM,which is incorrect.
Here's the sector that contains the directory.ProDiscover incorrectly reports it as full of SPAM.
Here is HxD, showing the correct contents ofsector 2 (all zeroes):
Here's the actual directory on the disk.It's not full of SPAM, of course.
Thanks to 'var x' for help with the hardware.
Downloadable Test Images
I made some images anyone can use to seethis problem, and to test the next versionwhen it comes out.To use them, do these three steps:
1. Download & Extract
Download the file you prefer(DD or E01 format) and extract with 7-zip.Each archive contains a text file with hashesto verify accuracy, if you wish to.
2. View in ProDiscover
Open the image in ProDiscover and look at the contentsof cluster 3:Prodiscover Basic Videos
3. View in Another Tool
Open the image in HxD or any other tool and look at the contentsof cluster 3. You can easily see that the contents are notthe same:FAT32 Test Images
How These Images Were Made
I made a FAT32 partition, copied a textfile to it, and zeroed its first cluster addressin the FAT. I captured an image of thatwith FTK Imager.Then I converted that disk to NTFS with theWindows command-line tool CONVERTto create the NTFS sample partition. I acquired itwith FTK Imager.
Thanks to 'varx' for the idea to CONVERT the disk.
Vendor Notification
I emailed the vendor on 1-23-13 about problem #1.Posted by Sam Bowne, 8:10 PM, Jan 23, 2013Prodiscover Basic Free Download
Problem #2 added 8:45 am, Jan 24, 2013Item #3 added 4:44 PM Jan 24, 2013
Video and vendor responses added 4:33 pm Jan. 25, 2013
Images redacted 5:28 pm Jan. 25, 2013
Image files added 1-26-13 9:18 pm